Fraud is an issue that affects organizations around the globe. As fraudsters become increasingly tech-savvy and strategic in their fraud schemes, it’s imperative that organizations stay a step ahead. Organizations can do so by cultivating awareness, implementing effective detection tools, and having a solid response and recovery plan in place.
In this article, we’ll explore the top fraud trends to watch in 2026 and share actionable strategies to help your company proactively prevent, detect, respond to, and recover from fraud. Is your organization prepared to meet the challenge?
Top 10 Fraud Trends to Watch in 2026
- Rise of Realistic AI-Driven Fraud: Artificial intelligence (AI) will be a double-edged sword, simultaneously powering sophisticated fraud prevention systems and increasingly convincing schemes by threat actors.
- AI-Driven Fraud & Deepfakes: Expect a surge in the use of deepfakes for fraudulent activities. Cybercriminals are using AI to craft convincing phishing emails and deepfakes for impersonation and disinformation. These tools are also being used to bypass traditional security measures.
- Synthetic Identity Fraud & AI Voice Cloning: Fraudsters are leveraging AI to create new, fictitious identities by blending real and fake information and creating cloned voices of trusted individuals. They are difficult to detect and can be used to open fraudulent accounts, build credit, and commit various types of financial fraud.
- Risk of AI-Powered Job Scams: Fraudsters flood the market with realistic job listings for positions that don’t exist, collecting personal and sensitive information from applicants. On the flipside, automated mass applications are flooding recruiters with unqualified candidates, making it difficult to screen for genuine applicants. AI-assisted interviews can provide scripted answers to technical questions during interviews, making it more challenging to determine if a screened applicant is qualified.
- Nation-State Cyber Activity: State-affiliated actors are targeting critical infrastructure and financial sectors. Their operations are sophisticated, often involving espionage and retaliatory attacks.
- Third-Party & Supply Chain Vulnerabilities: Threat actors are exploiting weak links in third-party vendors and supply chain ecosystems to gain unauthorized access. This can lead to data breaches, service disruptions, and reputational damage.
- Cryptocurrency & Ransomware Evolution: The anonymity of crypto transactions is complicating efforts to trace illicit activities. Ransomware tactics are evolving to evade detection more effectively.
- Weak Internal Controls: A poor control environment, characterized by inadequate oversight, lack of segregation of duties, and outdated policies, creates fertile ground for fraud. These weaknesses enable embezzlement, unauthorized transactions, and manipulation of financial records, often going undetected until significant damage is done.
- Operational Inefficiencies as Fraud Enablers: Inefficient or poorly designed processes can lead to resource waste, missed anomalies, and increased exposure to fraud. When workflows are overly manual, siloed, or lack real-time monitoring, they become vulnerable to exploitation by both internal and external actors.
- Asset Misappropriation Schemes: Fraud occurs internally, where an employee steals or misuses their organization’s resources. Data monitoring (such as analyzing vendor payment trends and looking for shared attributes between employees and vendors) and a fraud, ethics, and compliance third-party hotline should be at the top of your list of priorities to consider.
Understanding these emerging fraud trends is only the first step. Equipping your organization with strategies to prevent, detect, respond to, and recover from fraud is where the challenge begins.
Gain Insights From Our Leaders Across the Globe
How do you see emerging fraud trends impacting organizations, and what role should leadership play in staying ahead?
Prevent, Detect, Respond, & Recover
Fraud Strikes. How Do You Respond & Recover?
When fraud strikes, whether internal or external in origination, organizations must act swiftly, strategically, and collaboratively. The first hours and days following discovery are critical, requiring a balance of urgency and precision. A well-prepared response plan, supported by legal, finance, internal audit, cybersecurity, and investigative teams, can help assess and contain damage, preserve evidence, and guide recovery. The following outlines key actions across three essential areas—investigations, cybersecurity, and internal audit—to help organizations navigate the immediate aftermath and strengthen future fraud resilience.
Investigations
In the first 72 hours after discovering occupational fraud, organizations should act deliberately and strategically. Preparation beforehand is key, including having a flexible response plan and the right resources. Upon discovery, it’s crucial to avoid impulsive actions and preserve evidence. Within the first day, leadership from the affected organization should define investigation goals, gauge risks, and assemble a capable, independent team. By the second day, evidence collection and interviews should begin, following a structured approach. By the third day, the plan should be refined based on new findings, with clear communication to stakeholders and a continued focus on the investigation’s objectives.
Cybersecurity Measures
When a cyber-related fraud incident occurs, an organization’s response can determine the difference between a manageable event and a full-blown crisis. A robust incident response and recovery plan can help lessen financial and reputational damage while restoring business operations swiftly and securely:
- Phase 1: Incident Response – “Stop the Bleeding”
- The immediate goal after detecting fraud is to contain the threat and prevent further damage.
- Containment and isolation are both key, the digital equivalent of quarantining a sick patient. Stop fraud from spreading across the network.
- Digital forensics and investigation is next. Once contained, it is essential to understand what happened, through a technical investigation.
- Phase 2: Recovery – “Get Back to Business”
- Eradication and system restoration begins. Clean up the mess and rebuild, either from unaffected backups or re-imaging, and patch vulnerabilities in the process.
- Post-incident hardening and validation will help strengthen your organization and improve resilience.
Internal Audit
When fraud occurs, internal audit is often involved to help gauge the overall impact of the fraud on the entire organization. Several areas where internal audit gets involved include:
- Coordination of the initial response or investigation, engaging multiple corporate functions including legal, finance, HR, compliance, and IT.
- Assessing the overall scope, depth, and breadth of fraud, including whether the organization is still at risk.
- Assisting in quantifying the financial, reputational, and compliance impact.
- Evaluating the control environment and remediation efforts.
Gain Insights From Our Leaders Across the Globe
What’s the number one takeaway for organizations around risk management when recovering from a fraud event?
The Damage Is Done. How Do You Prevent & Detect the Next Strike?
Recovering from fraud is only half the battle. A crucial next step is strengthening your defenses to prevent another incident. This begins with establishing the “tone at the top,” where leadership consistently champions a culture of integrity and accountability. The following strategies are essential pillars that reinforce this tone, turning a top-down mandate into an organization wide commitment to fraud prevention and detection.
Fraud Training
Organizations should train their personnel to look out for suspicious communications or behavior. Organizations also should confirm with their personnel that they are empowered to report anything suspicious and without negative repercussions; this should be communicated frequently and clearly.
Implementing Prevention & Detection Tools
Proactive data monitoring detects fraud faster than any other method, with a median detection time of six months. Yet, according to the Association of Certified Fraud Examiners (ACFE), only 53% of large organizations and 19% of small ones use it.1
Payment Risk Analytics
Our Payment Risk Analytics tool can help detect and mitigate fraud risks, improve internal controls, and gain deeper insights into:
- Conflicts of interest
- Acceleration patterns
- Risk scoring
The quickest way to detect fraud is with automated transaction and data monitoring. Leverage this approach by deploying your own data analytics to monitor for fraud. You can use risk assessments to identify the highest risk areas of your organization, then implement analytics targeted at those areas, such as Payment Risk Analytics, to proactively be on the lookout for fraud within your accounts payable, payroll, or purchasing card processes.
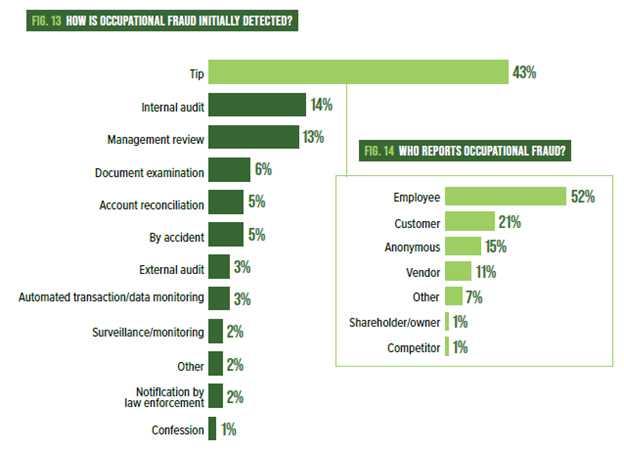
Figure 1: ACFE’s Occupational Fraud 2024: A Report to the Nations
IntegraReport®
We live in an age where seemingly everyone wants to be more data-driven and fraud prevention is an ideal opportunity to do just that. Let’s use the following data point provided by ACFE above. First, the most common method for detecting fraud is by a tip, meaning someone alerted management about the possible occurrence of fraud.
Consider setting up a third-party hotline reporting platform, such as IntegraReport, so your personnel, vendors, or customers can submit anonymous reports via whichever method they feel most comfortable with, whether through an online submission or by picking up the phone. Implementing an anonymous fraud, ethics, and compliance reporting hotline service helps reinforce the leadership tone that misconduct and unethical behavior are not acceptable, creates a “speak up” culture by creating an avenue for reporting and a protective, serves as an anonymous mechanism to thwart potential retaliation, and demonstrates to regulators and stakeholders that the organization takes compliance seriously.
Both methods not only facilitate the detection of fraud but also serve as strong deterrents by setting a strong tone at the top, letting employees know that not only is fraud unacceptable, but that you’re actively keeping an eye out for it.
Risk Assessments as a Fraud & Cybersecurity Defense Mechanism
Risk assessment, particularly cybersecurity risk assessments, are critical tools for strengthening an organization’s cyber posture and reducing fraud-related risks. By systematically identifying vulnerabilities across systems, processes, and personnel, these assessments enable organizations to prioritize controls that safeguard sensitive data and prevent exploitation. A robust cybersecurity risk assessment framework evaluates threats such as ransomware, phishing, insider abuse, and third-party risks, and aligns with standards such as the Cyber Risk Institute (CRI) Profile, National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF), and International Organization for Standardization (ISO) 27001, to maintain consistency and compliance. Beyond technical safeguards, risk assessments also address human factors, which are often the root cause of breaches and fraud incidents.
The following actions can help mitigate cyber fraud risks, enhance resilience, and help ensure your systems and personnel are prepared to detect, respond to, and recover from cyberthreats:
- Conduct Regular Cybersecurity Risk Assessments: Use structured frameworks to identify gaps and prioritize remediation efforts before incidents occur.
- Implement Layered Security Controls: Combine firewalls, encryption, multifactor authentication, and endpoint protection to reduce attack surfaces.
- Enhance Employee Awareness: Deliver ongoing fraud and cybersecurity training to reduce social engineering and phishing risks.
- Monitor & Test Continuously: Deploy vulnerability scanning, penetration testing, and anomaly detection to identify weaknesses early.
- Establish Incident Response & Reporting Mechanisms: Create clear protocols for responding to cyber events and implement anonymous fraud hotlines to encourage early detection and reporting.
- Integrate Vendor Risk Management: Scrutinize third-party security practices to prevent supply chain vulnerabilities.
Evaluate Control Failures
Performing a post-mortem root-cause analysis is key in uncovering where controls were absent, poorly designed, and/or failed. To help strengthen your defenses and prevent future incidents, consider these key steps:
- Identify which internal controls were bypassed or failed.
- Assess the effectiveness of fraud detection mechanisms.
- Document gaps and recommend improvements.
- Implement, verify, and test.
Gain Insights From Our Leaders Across the Globe
Based on your experience, where do you see the most significant gaps in your clients’ fraud prevention strategies?
End-to-End Fraud Risk Support With Forvis Mazars
Navigating fraud requires a multifaceted approach. At Forvis Mazars, we can help you tackle today’s challenges head-on with an experienced team of analytics, cybersecurity, forensics, and internal audit professionals, providing organizations end-to-end fraud risk support. Our integrated services combine extensive skills with cutting-edge technology and strategic insights. Whether you need to investigate a suspected incident, implement detection tools like Payment Risk Analytics, establish a third-party hotline platform such as IntegraReport, or strengthen your internal controls, we are ready to help you prepare for what’s next. If you have any questions or need assistance, reach out to a professional at Forvis Mazars.
- 1“Occupational Fraud 2024: A Report to the Nations,” legacy.acfe.com, 2025.
Access essential tips to help future proof your fraud risk strategy!
Download Now